Who is the genius behind the creation of the Tor Onion browser? Tor is an anonymous web browser that has become synonymous with online privacy and anonymity. Tor facilitated deep web and dark web and allows users to access the dark web and deep web without leaving a digital footprint. While the exact identity of the creator remains a mystery. But what we do know is that the Tor Project, a non-profit organization, developed and maintains the browser.
Furthermore, this project was founded in the early 2000s by a group of computer scientists and mathematicians who were committed to promoting online privacy and freedom of expression. Their efforts have been instrumental in providing a secure platform for millions of users worldwide to communicate, research, and access information without the fear of surveillance or censorship.
So, let us learn as we delve into the fascinating world of Tor, exploring its origins, functionality, and the team of brilliant minds behind its creation and how the Tor browser facilitated the Deep Web Links.
The History of the Tor Onion Browser
The history of the Tor Onion browser can be traced back to the late 1990s when the need for online privacy and anonymity started gaining traction. A group of computer scientists and mathematicians, known as the Cypherpunks, were at the forefront of this movement. They planned a world where individuals could freely communicate and access information without the fear of being monitored or censored.
In 2002, the Tor Project was officially founded by Roger Dingledine, Nick Mathewson, and Paul Syverson. They aimed to develop a tool that could protect users’ privacy by directing their internet traffic through a network of volunteer-operated servers known as nodes. This network, known as the Tor network, would make it difficult for anyone to track the origin and last stop of the user’s online activities.
Over the years, the Tor Project has grown and advanced, with contributions from a global community of developers and volunteers. Right now, the Tor Onion browser is one of the most popular tools for accomplishing online privacy and anonymity. It is used by activists, journalists, whistleblowers, and everyday internet users.
Despite its origins in the pursuit of privacy and freedom, the Tor Onion browser has confronted its fair share of controversies and criticisms. Some argue that the Tor platform facilitated anonymous communication and empowers illegal activities, such as drug trafficking and child exploitation on the deep web. However, the Tor Project maintains that its primary focus is on honoring human rights, civil liberties, and the right to privacy.
The Tor Project and its Mission
The Tor Project is a non-profit organization devoted to developing and maintaining tools that endorse online privacy and freedom of expression. Their mission is to advance human rights and defend against surveillance and censorship. The Tor onion browser is one of the key projects started by the organization, together with other initiatives such as the Tor network and Tor relays.
The Tor Project operates on the principles of transparency, openness, and decentralization. Its development process is community-driven, with contributions from volunteers and developers worldwide. The organization also conducts research and collaborates with academic institutions to improve the security and usability of its tools.
One of the key goals of the Tor Project is to provide a secure platform for people living in oppressive regimes to access data and connect without restrictions. In countries where internet censorship and surveillance are prevalent, the Tor Onion browser can help individuals avoid these restrictions and protect their privacy.
The Tor Project also actively works to instruct the public about online privacy and security. The organization aims to empower individuals and organizations. Via numerous initiatives to protect their online privacy and take control of their digital lives. The initiatives include the Tor Training Portal and the Tor Relay Guide,
How does the Tor Onion Browser Work?
The Tor onion browser encrypts and routes the internet traffic through a series of volunteer-operated nodes. When a user accesses the internet through the Tor browser, their traffic is encrypted and sent through multiple nodes before reaching its destination. This process makes it difficult for anyone to trace the user’s online activities back to their original IP address.
The Tor network consists of thousands of relays, which are computers operated by volunteers around the world. These relays act as intermediaries, passing encrypted data between each other until it reaches the final destination. Each relay only knows the IP address of the previous and next relay in the chain, ensuring that no single relay has complete knowledge of the entire route.
To further enhance privacy, the Tor onion browser also employs a technique called onion routing. This involves encrypting the user’s data multiple times, creating layers like an onion. Each relay in the network peels back one layer of encryption, revealing only the information required to pass the data to the next relay. This multi-layered encryption ensures that even if a relay is compromised, the user’s privacy remains intact.
It is important to note that while the Tor onion browser provides a high level of anonymity, it does not guarantee complete security. Users should still exercise caution when accessing sensitive information or engaging in activities that may attract unwanted attention.
Features and Benefits of Using the Tor Onion Browser
The Tor Onion browser offers several features and benefits that make it an attractive option for individuals seeking online privacy and anonymity.
- Anonymity: By routing internet traffic through a network of relays, the Tor Onion browser helps users maintain their anonymity online. It makes it difficult for anyone, including internet service providers, governments, and hackers, to track their online activities.
- Circumvention of censorship: In countries where internet censorship is prevalent, the Tor Onion browser can be a valuable tool for accessing blocked websites and bypassing restrictions. It allows individuals to communicate and access information freely without fear of government surveillance or censorship.
- Protection against surveillance: The Tor onion browser encrypts the user’s internet traffic, making it difficult for surveillance agencies to intercept and monitor their online activities. This is particularly important for individuals who live in countries with a history of surveillance and human rights abuses.
- Secure communication: The Tor Onion browser provides a secure platform for individuals to communicate privately and securely. It can be used to send encrypted messages, access secure email services, and engage in anonymous online discussions.
- Support for whistleblowers and journalists: The Tor Onion browser has become an essential tool for whistleblowers and journalists who need to protect their sources and communicate securely. It enables them to share sensitive information without fear of reprisal or exposure.
Controversies Surrounding the Tor Onion Browser
The Tor onion browser has faced its fair share of controversies and criticisms since its inception. One of the main concerns raised by critics is the potential for the browser to be exploited for illegal activities. Because of its anonymous nature, some individuals may use the Tor Onion browser to engage in illegal activities. Like drug trafficking, child exploitation, or hacking.
However, it is crucial to note that the Tor Project has not endorsed or facilitated any illegal activities on the deep web and dark web. The organization’s primary focus is on promoting human rights, civil liberties, and the right to privacy. They actively collaborate with law enforcement agencies to combat illegal activities on the network and maintain a balance between privacy and security.
Another controversy surrounding the Tor onion browser is the potential for malicious exit nodes. Since the Tor network relies on volunteer-operated nodes, there is a possibility that some of these nodes may be compromised or operated with malicious intent. This could potentially expose users’ data or compromise their anonymity.
To mitigate this risk, the Tor Project employs various security measures. Such as regularly monitoring the network for anomalies, conducting audits of the codebase, and providing guidelines for running secure Tor relays. Additionally, users can further enhance their security by using end-to-end encryption and being cautious about the websites they visit and the information they share.
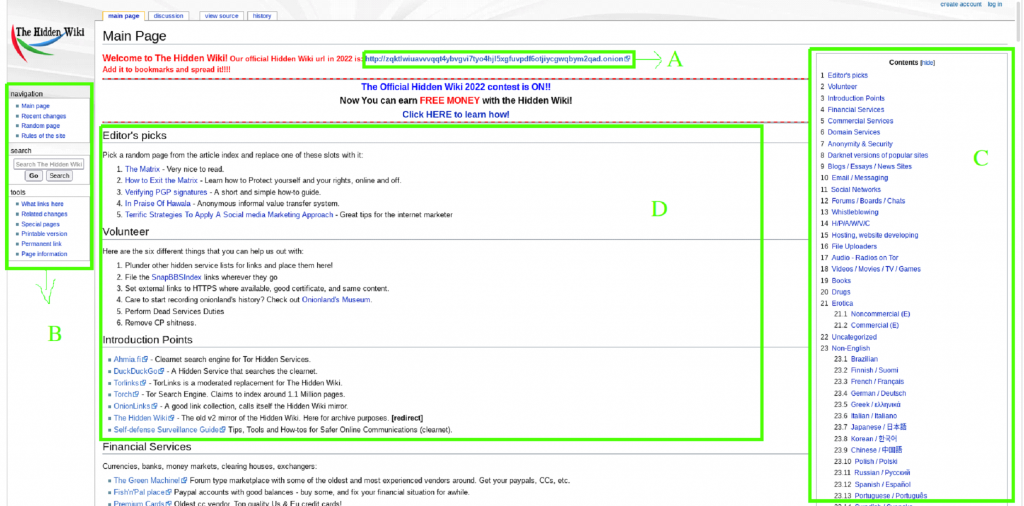
How the Tor Facilitated Deep Web Links
Tor, an abbreviation of The Onion Router, is a free and open-source software that allows anonymous communication. It achieves this by bouncing internet traffic through a network of volunteer-run servers, known as nodes, effectively masking the user’s IP address. This network of nodes makes it extremely difficult for anyone to trace the user’s online activities back to their original IP address.
Tor Browser, a modified version of the Mozilla Firefox browser, is specifically designed to work with the Tor network. It allows users to access deep web links by routing their internet traffic through multiple layers of encryption and relays. This ensures that users can explore the deep web while maintaining their anonymity and privacy.
How the Tor Browser Provides Anonymity and Security for Deep Web Users
The Tor browser facilitated anonymity and security, which is why many users turn to the Tor browser to access the deep web. When a user connects to the Tor network, their internet traffic is encrypted and routed through a series of random nodes before reaching its destination. This makes it extremely difficult for anyone, including internet service providers, government agencies, or hackers, to intercept and trace the user’s online activities.
In addition to encryption, the Tor Browser also prevents websites from tracking users through features. Such as blocking third-party cookies and turning off certain web technologies that can be used to identify users. It also includes built-in features like HTTPS Everywhere, which ensures that the user’s connection to websites is encrypted whenever possible.
Understanding the Dark Web and its Relationship to Deep Web Links
While the terms “deep web” and “dark web” are often used interchangeably, they refer to different parts of the internet. The deep web encompasses all the content that is not indexed by search engines, including both legal and illegal content. On the other hand, the dark web refers specifically to the part of the deep web that is intentionally hidden and often associated with illegal activities.
Deep web links can lead to both legal and illegal content, depending on the nature of the websites they point to. While the Tor Browser facilitated access to both the deep web and the dark web links. But it’s important to note that not all deep web links lead to illegal or dangerous content. Many deep web websites are legitimate platforms for sharing information, providing privacy-focused services, or hosting communities that value anonymity.
How the Tor Browser Has Impacted Online Privacy and Censorship
The introduction of Tor Browser has had a significant impact on online privacy and censorship. It has given individuals the means to access information, communicate, and express themselves without fear of surveillance or censorship. Tor Browser has been widely used by journalists, activists, and individuals living under oppressive regimes to bypass censorship and access information that would otherwise be restricted.
However, the use of Tor Browser has also raised concerns among governments and law enforcement agencies. Its ability to provide anonymity has been exploited by criminals for illegal activities, making it a subject of scrutiny and regulation. Balancing the need for privacy and security in the digital age remains an ongoing challenge, with Tor Browser at the forefront of this debate.
Security and Privacy Considerations when Using the Tor Onion Browser
The Tor Onion browser facilitated a high level of anonymity and privacy to access the deep web. That is why users need to be aware of certain security and privacy considerations.
- Endpoint Security: The Tor onion browser can protect the user’s online activities up to the exit node. However, once the data leaves the Tor network and reaches the destination website, it is no longer encrypted. Therefore, it is essential to ensure that the websites visited are secure and employ encryption (HTTPS) to protect sensitive information.
- Additional Security Measures: Users can further enhance their security by using additional security measures. Such as end-to-end encryption, strong passwords, and regularly updating their software and operating systems.
- Browsing Habits: While the Tor Onion browser can provide anonymity, users need to be mindful of their browsing habits. Certain activities can compromise anonymity and privacy, such as logging into personal accounts and sharing personally identifiable information.
- Trustworthy Sources: When using the Tor Onion browser, it is important to access information from trustworthy sources. Some malicious actors may set up fake websites or phishing sites to collect user information. Verifying the authenticity of websites and sources is crucial to maintaining security and privacy.
The Future of Deep Web Links and the Tor Browser
Tor Browser has revolutionized the way we access the deep web. It provides a gateway to hidden realms while prioritizing privacy and security. Deep web links, facilitated by Tor Browser, offer a glimpse into a world that is not readily accessible through traditional search engines. However, navigating the deep web also comes with risks and responsibilities.
As technology continues to evolve, the future of deep web links and the Tor Browser remains uncertain. Both will likely adapt and evolve to meet the changing needs and challenges of the digital age. The balance between privacy and security will continue to be a delicate one.
The Top 4 Alternatives to the Tor Onion Browser
The Tor onion browser is a popular choice for online privacy and anonymity. There are alternative tools and browsers available that offer similar functionality. Some of the Tor alternatives include:
- I2P: The Invisible Internet Project (I2P) is an anonymous overlay network that allows users to access websites and services anonymously. It provides a decentralized and encrypted network for secure communication.
- Freenet: Freenet is a peer-to-peer network that enables users to share files, publish websites, and communicate anonymously. It aims to provide censorship-resistant and decentralized access to information.
- VPN (Virtual Private Network): A VPN allows users to create a secure, encrypted connection to another network over the internet. It can help protect privacy and mask the user’s IP address, making it difficult for anyone to track their online activities.
- Proxy Servers: Proxy servers act as intermediaries between the user’s device and the internet. They can help users bypass censorship and access blocked websites while also providing an additional layer of anonymity.
It is important to research and evaluate the features, security, and privacy policies of these alternatives to determine which one best suits individual needs and preferences.
Wrap Up
The Tor onion browser has revolutionized the way we think about online privacy and anonymity. While the exact identity of the creator remains unknown. The Tor Project and its team of brilliant minds have made significant contributions to the development and maintenance of this powerful tool. The Tor Onion browser has enabled millions of users worldwide to communicate, research, and access information. Also, access deep web links without the fear of surveillance or censorship.
Join us as we explore the fascinating world of deep web links facilitated by Tor Browser, understanding the risks and benefits associated with this hidden part of the internet. Discover the hidden wonders and complexities of the deep web and gain insights into the ongoing discussions surrounding online privacy, and censorship. The deep web awaits, and Tor Browser is your key to unlocking its secrets.